Circuits
This page explains circuits.
3.1.5 Current flows in closed loops called circuits. These circuits must be made of conductive materials and must have sources of voltage. Voltage causes current to flow. Resistance and impedance oppose it. Current consists of electrons that flow away from negative terminals and toward positive terminals. These facts allow people to control the flow of current.
Electricity will naturally flow to the earth if there is a path. Current also flows along the path of least resistance. If a human body provides the path of least resistance, the current will flow through it. When an electric appliance has a plug with three prongs, one of the prongs acts as the ground, or 0 volts. The ground provides a conductive path for the electrons to flow to the earth. The resistance of the body would be greater than the resistance of the ground.
Ground typically means the 0-volts level in reference to electrical measurements. Voltage is created by the separation of charges, which means that voltage measurements must be made between two points.
A water analogy can help explain the concept of electricity. The higher the water and the greater the pressure, the more the water will flow. The water current also depends on the size of the space it must flow through. Similarly, the higher the voltage and the greater the electrical pressure, the more current will be produced. The electric current then encounters resistance that, like the water tap, reduces the flow. If the electric current is in an AC circuit, then the amount of current will depend on how much impedance is present. If the electric current is in a DC circuit, then the amount of current will depend on how much resistance is present. The pump is like a battery. It provides pressure to keep the flow moving.
The relationship among voltage, resistance, and current is voltage (V) equals current (I) multiplied by resistance (R). In other words, V=I*R. This is Ohm’s law, named after the scientist who explored these issues.
Two ways in which current flows are alternating current (AC) and direct current (DC). AC voltages change their polarity, or direction, over time. AC flows in one direction, then reverses its direction and flows in the other direction, and then repeats the process. AC voltage is positive at one terminal, and negative at the other. Then the AC voltage reverses its polarity, so that the positive terminal becomes negative, and the negative terminal becomes positive. This process repeats itself continuously.
DC always flows in the same direction and DC voltages always have the same polarity. One terminal is always positive, and the other is always negative. They do not change or reverse.
An oscilloscope is an electronic device used to measure electrical signals relative to time. An oscilloscope graphs the electrical waves, pulses, and patterns. An oscilloscope has an x-axis that represents time, and a y-axis that represents voltage. There are usually two y-axis voltage inputs so that two waves can be observed and measured at the same time.
Power lines carry electricity in the form of AC because it can be delivered efficiently over large distances. DC can be found in flashlight batteries, car batteries, and as power for the microchips on the motherboard of a computer, where it only needs to go a short distance.
Electrons flow in closed circuits, or complete loops. Figure shows a simple circuit. The chemical processes in the battery cause charges to build up. This provides a voltage, or electrical pressure, that enables electrons to flow through various devices. The lines represent a conductor, which is usually copper wire. Think of a switch as two ends of a single wire that can be opened or broken to prevent the flow of electrons. When the two ends are closed, fixed, or shorted, electrons are allowed to flow. Finally, a light bulb provides resistance to the flow of electrons, which causes the electrons to release energy in the form of light. The circuits in networks use a much more complex version of this simple circuit.
For AC and DC electrical systems, the flow of electrons is always from a negatively charged source to a positively charged source. However, for the controlled flow of electrons to occur, a complete circuit is required. Figure shows part of the electrical circuit that brings power to a home or office.
The Lab Activity explores the basic properties of series circuits.
The next page covers cable specifications.
Cable specifications
3.1.6 Cables have different specifications and expectations. Important considerations related to performance are as follows:
• What speeds for data transmission can be achieved? The speed of bit transmission through the cable is extremely important. The speed of transmission is affected by the kind of conduit used.
• Will the transmissions be digital or analog? Digital or baseband transmission and analog or broadband transmission require different types of cable.
• How far can a signal travel before attenuation becomes a concern? If the signal is degraded, network devices might not be able to receive and interpret the signal. The distance the signal travels through the cable affects attenuation of the signal. Degradation is directly related to the distance the signal travels and the type of cable used.
The following Ethernet specifications relate to cable type:
• 10BASE-T
• 10BASE5
• 10BASE2
10BASE-T refers to the speed of transmission at 10 Mbps. The type of transmission is baseband, or digitally interpreted. The T stands for twisted pair.
10BASE5 refers to the speed of transmission at 10 Mbps. The type of transmission is baseband, or digitally interpreted. The 5 indicates that a signal can travel for approximately 500 meters before attenuation could disrupt the ability of the receiver to interpret the signal. 10BASE5 is often referred to as Thicknet. Thicknet is a type of network and 10BASE5 is the cable used in that network.
10BASE2 refers to the speed of transmission at 10 Mbps. The type of transmission is baseband, or digitally interpreted. The 2, in 10BASE2, refers to the approximate maximum segment length being 200 meters before attenuation could disrupt the ability of the receiver to appropriately interpret the signal being received. The maximum segment length is actually 185 meters. 10BASE2 is often referred to as Thinnet. Thinnet is a type of network and 10BASE2 is the cable used in that network.
The next page describes coaxial cable.
Coaxial cable
3.1.7 Coaxial cable consists of a copper conductor surrounded by a layer of flexible insulation. The center conductor can also be made of tin plated aluminium cable allowing for the cable to be manufactured inexpensively. Over this insulating material is a woven copper braid or metallic foil that acts as the second wire in the circuit and as a shield for the inner conductor. This second layer, or shield also reduces the amount of outside electromagnetic interference. Covering this shield is the cable jacket.
For LANs, coaxial cable offers several advantages. It can be run longer distances than shielded twisted pair, STP, unshielded twisted pair, UTP, and screened twisted pair, ScTP, cable without the need for repeaters. Repeaters regenerate the signals in a network so that they can cover greater distances. Coaxial cable is less expensive than fiber-optic cable and the technology is well known. It has been used for many years for many types of data communication such as cable television.
It is important to consider the size of a cable. As the thickness increases, it becomes more difficult to work with a cable. Remember that cable must be pulled through conduits and troughs that are limited in size. Coaxial cable comes in a variety of sizes. The largest diameter was specified for use as Ethernet backbone cable since it has greater transmission lengths and noise rejection characteristics. This type of coaxial cable is frequently referred to as Thicknet. This type of cable can be too rigid to install easily in some situations. Generally, the more difficult the network media is to install, the more expensive it is to install. Coaxial cable is more expensive to install than twisted-pair cable. Thicknet cable is rarely used anymore aside from special purpose installations.
In the past, Thinnet coaxial cable with an outside diameter of only 0.35 cm was used in Ethernet networks. It was especially useful for cable installations that required the cable to make many twists and turns. Since Thinnet was easier to install, it was also cheaper to install. This led some people to refer to it as Cheapernet. The outer copper or metallic braid in coaxial cable comprises half the electric circuit. A solid electrical connection at both ends is important to properly ground the cable. Poor shield connection is one of the biggest sources of connection problems in the installation of coaxial cable. Connection problems result in electrical noise that interferes with signal transmission. For this reason Thinnet is no longer commonly used nor supported by latest standards, 100 Mbps and higher, for Ethernet networks.
The following page describes STP cable.
Monday, December 7, 2009
Copper Media / Atoms and electrons / Voltage / Resistance and impedance / Current
Atoms and electrons
3.1.1 This lesson discusses the copper media used in networking. Since all matter is composed of atoms, this page begins with a detailed explanation of atoms and electrons.
All matter is composed of atoms. The Periodic Table of Elements lists all known types of atoms and their properties. The atom is comprised of three basic particles:
• Electrons – Particles with a negative charge that orbit the nucleus
• Protons – Particles with a positive charge
• Neutrons – Neutral particles with no charge
The protons and neutrons are combined together in a small group called a nucleus.
To better understand the electrical properties of different elements, locate helium (He) on the periodic table. Helium has an atomic number of 2, which means that helium has two protons and two electrons. It has an atomic weight of 4. If the atomic number of 2 is subtracted from the atomic weight of 4, the result shows that helium also has two neutrons.
The Danish physicist, Niels Bohr, developed a simplified model to illustrate the atom. This illustration shows the model for a helium atom. If the protons and neutrons of an atom were the size of adult soccer balls in the middle of a soccer field, the only thing smaller than the balls would be the electrons. The electrons would be the size of cherries that would be in orbit near the outer-most seats of the stadium. The overall volume of this atom would be about the size of the stadium. The nucleus would be the size of the soccer balls.
Coulomb's Electric Force Law states that opposite charges react to each other with a force that causes them to be attracted to each other. Like charges react to each other with a force that causes them to repel each other. In the case of opposite and like charges, the force increases as the charges move closer to each other. The force is inversely proportional to the square of the separation distance. When particles get extremely close together, nuclear force overrides the repulsive electrical force and keeps the nucleus together. That is why a nucleus does not fly apart.
Examine the Bohr model of the helium atom. If Coulomb's law is true and the Bohr model describes helium atoms as stable, then there must be other laws of nature at work. Review both theories to see how they conflict with each other:
• Coulomb's law – Opposite charges attract and like charges repel.
• The Bohr model – Protons have positive charges and electrons have negative charges. There is more than one proton in the nucleus.
Electrons stay in orbit, even though the protons attract the electrons. The electrons have just enough velocity to keep orbiting and not be pulled into the nucleus, just like the moon around the Earth.
Protons do not fly apart from each other because of a nuclear force that is associated with neutrons. The nuclear force is an incredibly strong force that acts as a kind of glue to hold the protons together.
Electrons are bound to their orbit around the nucleus by a weaker force than nuclear force. Electrons in certain atoms, such as metals, can be pulled free from the atom and made to flow. This sea of electrons, loosely bound to the atoms, is what makes electricity possible. Electricity is a free flow of electrons.
Loosened electrons that do not move and have a negative charge are called static electricity. If these static electrons have an opportunity to jump to a conductor, this can lead to electrostatic discharge (ESD). Conductors will be discussed later in this module.
ESD is usually harmless to people. However, ESD can create serious problems for sensitive electronic equipment. A static discharge can randomly damage computer chips, data, or both. The logical circuitry of computer chips is extremely sensitive to ESD. Students should take safety precautions before they work inside computers, routers, and similar devices.
Atoms, or groups of atoms called molecules, can be referred to as materials. Materials are classified into three groups based on how easily free electrons flow through them.
The basis for all electronic devices is the knowledge of how insulators, conductors, and semiconductors control the flow of electrons and work together.
The Lab Activity reviews the proper way to handle a multimeter.
The next page introduces voltage.
Voltage
3.1.2 Voltage is sometimes referred to as electromotive force (EMF). EMF is related to an electrical force, or pressure, that occurs when electrons and protons are separated. The force that is created pushes toward the opposite charge and away from the like charge. This process occurs in a battery, where chemical action causes electrons to be freed from the negative terminal of the battery. The electrons then travel to the opposite, or positive, terminal through an external circuit. The electrons do not travel through the battery. Remember that the flow of electricity is really the flow of electrons. Voltage can also be created in three other ways. The first is by friction, or static electricity. The second way is by magnetism, or an electric generator. The last way that voltage can be created is by light, or a solar cell.
Voltage is represented by the letter V, and sometimes by the letter E, for electromotive force. The unit of measurement for voltage is volt (V). A volt is defined as the amount of work, per unit charge, that is needed to separate the charges.
The next page describes resistance and impedance.
This page explains the concepts of resistance and impedance.
Resistance and impedance
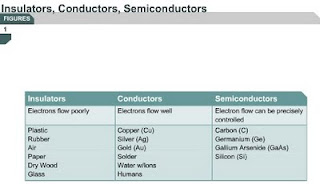
3.1.3 The materials through which current flows vary in their resistance to the movement of the electrons. The materials that offer very little or no resistance are called conductors. Those materials that do not allow the current to flow, or severely restrict its flow, are called insulators. The amount of resistance depends on the chemical composition of the materials.
All materials that conduct electricity have a measure of resistance to the flow of electrons through them. These materials also have other effects called capacitance and inductance that relate to the flow of electrons. Impedance includes resistance, capacitance, and inductance and is similar to the concept of resistance.
Attenuation is important in relation to networks. Attenuation refers to the resistance to the flow of electrons and explains why a signal becomes degraded as it travels along the conduit.
The letter R represents resistance. The unit of measurement for resistance is the ohm (Ω). The symbol comes from the Greek letter omega.
Electrical insulators are materials that are most resistant to the flow of electrons through them. Examples of electrical insulators include plastic, glass, air, dry wood, paper, rubber, and helium gas. These materials have very stable chemical structures and the electrons are tightly bound within the atoms.
Electrical conductors are materials that allow electrons to flow through them easily. The outermost electrons are bound very loosely to the nucleus and are easily freed. At room temperature, these materials have a large number of free electrons that can provide conduction. The introduction of voltage causes the free electrons to move, which results in a current flow.
The periodic table categorizes some groups of atoms in the form of columns. The atoms in each column belong to particular chemical families. Although they may have different numbers of protons, neutrons, and electrons, their outermost electrons have similar orbits and interactions with other atoms and molecules. The best conductors are metals such as copper (Cu), silver (Ag), and gold (Au). These metals have electrons that are easily freed. Other conductors include solder, which is a mixture of lead (Pb) and tin (Sn), and water with ions. An ion is an atom that has a different number of electrons than the number of protons in the nucleus. The human body is made of approximately 70 percent water with ions, which means that it is a conductor.
Semiconductors are materials that allow the amount of electricity they conduct to be precisely controlled. These materials are listed together in one column of the periodic chart. Examples include carbon (C), germanium (Ge), and the alloy gallium arsenide (GaAs). Silicon (Si) is the most important semiconductor because it makes the best microscopic-sized electronic circuits.
Silicon is very common and can be found in sand, glass, and many types of rocks. The region around San Jose, California is known as Silicon Valley because the computer industry, which depends on silicon microchips, started in that area.
The next page describes electrical current
Current
3.1.4 Electrical current is the flow of charges created when electrons move. In electrical circuits, the current is caused by a flow of free electrons. When voltage is applied and there is a path for the current, electrons move from the negative terminal along the path to the positive terminal. The negative terminal repels the electrons and the positive terminal attracts the electrons. The letter I represents current. The unit of measurement for current is Ampere (A). An ampere is defined as the number of charges per second that pass by a point along a path.
Current can be thought of as the amount or volume of electron traffic that flows. Voltage can be thought of as the speed of the electron traffic. The combination of amperage and voltage equals wattage. Electrical devices such as light bulbs, motors, and computer power supplies are rated in terms of watts. Wattage indicates how much power a device consumes or produces.
It is the current or amperage in an electrical circuit that really does the work. For example, static electricity has such a high voltage that it can jump a gap of an inch or more. However, it has very low amperage and as a result can create a shock but not permanent injury. The starter motor in an automobile operates at a relatively low 12 volts but requires very high amperage to generate enough energy to turn over the engine. Lightning has very high voltage and high amperage and can cause severe damage or injury.
The next page discusses circuits.
Module 3: Networking Media / Overview
Overview
Copper cable is used in almost every LAN. Many different types of copper cable are available. Each type has advantages and disadvantages. Proper selection of cabling is key to efficient network operation. Since copper uses electrical currents to transmit information, it is important to understand some basics of electricity.
Optical fiber is the most frequently used medium for the longer, high bandwidth, point-to-point transmissions required on LAN backbones and on WANs. Optical media uses light to transmit data through thin glass or plastic fiber. Electrical signals cause a fiber-optic transmitter to generate the light signals sent down the fiber. The receiving host receives the light signals and converts them to electrical signals at the far end of the fiber. However, there is no electricity in the fiber-optic cable. In fact, the glass used in fiber-optic cable is a very good electrical insulator.
Physical connectivity allows users to share printers, servers, and software, which can increase productivity. Traditional networked systems require the workstations to remain stationary and permit moves only within the limits of the media and office area.
The introduction of wireless technology removes these restraints and brings true portability to computer networks. Currently, wireless technology does not provide the high-speed transfers, security, or uptime reliability of cabled networks. However, flexibility of wireless has justified the trade off.
Administrators often consider wireless when they install or upgrade a network. A simple wireless network could be working just a few minutes after the workstations are turned on. Connectivity to the Internet is provided through a wired connection, router, cable, or DSL modem and a wireless access point that acts as a hub for the wireless nodes. In a residential or small office environment these devices may be combined into a single unit.
This module covers some of the objectives for the CCNA 640-801, INTRO 640-821, and ICND 640-811 exams.
Students who complete this module should be able to perform the following tasks:
• Discuss the electrical properties of matter
• Define voltage, resistance, impedance, current, and circuits
• Describe the specifications and performances of different types of cable
• Describe coaxial cable and its advantages and disadvantages compared to other types of cable
• Describe STP cable and its uses
• Describe UTP cable and its uses
• Discuss the characteristics of straight-through, crossover, and rollover cables and where each is used
• Explain the basics of fiber-optic cable
• Describe how fiber-optic cables can carry light signals over long distances
• Describe multimode and single-mode fiber
• Describe how fiber is installed
• Describe the type of connectors and equipment used with fiber-optic cable
• Explain how fiber is tested to ensure that it will function properly
• Discuss safety issues related to fiber optics
Copper cable is used in almost every LAN. Many different types of copper cable are available. Each type has advantages and disadvantages. Proper selection of cabling is key to efficient network operation. Since copper uses electrical currents to transmit information, it is important to understand some basics of electricity.
Optical fiber is the most frequently used medium for the longer, high bandwidth, point-to-point transmissions required on LAN backbones and on WANs. Optical media uses light to transmit data through thin glass or plastic fiber. Electrical signals cause a fiber-optic transmitter to generate the light signals sent down the fiber. The receiving host receives the light signals and converts them to electrical signals at the far end of the fiber. However, there is no electricity in the fiber-optic cable. In fact, the glass used in fiber-optic cable is a very good electrical insulator.
Physical connectivity allows users to share printers, servers, and software, which can increase productivity. Traditional networked systems require the workstations to remain stationary and permit moves only within the limits of the media and office area.
The introduction of wireless technology removes these restraints and brings true portability to computer networks. Currently, wireless technology does not provide the high-speed transfers, security, or uptime reliability of cabled networks. However, flexibility of wireless has justified the trade off.
Administrators often consider wireless when they install or upgrade a network. A simple wireless network could be working just a few minutes after the workstations are turned on. Connectivity to the Internet is provided through a wired connection, router, cable, or DSL modem and a wireless access point that acts as a hub for the wireless nodes. In a residential or small office environment these devices may be combined into a single unit.
This module covers some of the objectives for the CCNA 640-801, INTRO 640-821, and ICND 640-811 exams.
Students who complete this module should be able to perform the following tasks:
• Discuss the electrical properties of matter
• Define voltage, resistance, impedance, current, and circuits
• Describe the specifications and performances of different types of cable
• Describe coaxial cable and its advantages and disadvantages compared to other types of cable
• Describe STP cable and its uses
• Describe UTP cable and its uses
• Discuss the characteristics of straight-through, crossover, and rollover cables and where each is used
• Explain the basics of fiber-optic cable
• Describe how fiber-optic cables can carry light signals over long distances
• Describe multimode and single-mode fiber
• Describe how fiber is installed
• Describe the type of connectors and equipment used with fiber-optic cable
• Explain how fiber is tested to ensure that it will function properly
• Discuss safety issues related to fiber optics
Thursday, November 19, 2009
Summary of 2nd Chapter (Module)
Summary
This page summarizes the topics discussed in this module.
Computer networks developed in response to business and government computing needs. Applying standards to network functions provided a set of guidelines for creating network hardware and software and provided compatibility among equipment from different companies. Information could move within a company and from one business to another.
Network devices, such as repeaters, hubs, bridges, switches and routers connect host devices together to allow them to communicate. Protocols provide a set of rules for communication.
The physical topology of a network is the actual layout of the wire or media. The logical topology defines how host devices access the media. The physical topologies that are commonly used are bus, ring, star, extended star, hierarchical, and mesh. The two most common types of logical topologies are broadcast and token passing.
A local-area network (LAN) is designed to operate within a limited geographical area. LANs allow multi-access to high-bandwidth media, control the network privately under local administration, provide full-time connectivity to local services and connect physically adjacent devices.
A wide-area network (WAN) is designed to operate over a large geographical area. WANs allow access over serial interfaces operating at lower speeds, provide full-time and part-time connectivity and connect devices separated over wide areas.
A metropolitan-area network (MAN) is a network that spans a metropolitan area such as a city or suburban area. A MAN usually consists of two or more LANs in a common geographic area.
A storage-area network (SAN) is a dedicated, high-performance network used to move data between servers and storage resources. A SAN provides enhanced system performance, is scalable, and has disaster tolerance built in.
A virtual private network (VPN) is a private network that is constructed within a public network infrastructure. Three main types of VPNs are access, Intranet, and Extranet VPNs. Access VPNs provide mobile workers or small office/home office (SOHO) users with remote access to an Intranet or Extranet. Intranets are only available to users who have access privileges to the internal network of an organization. Extranets are designed to deliver applications and services that are Intranet based to external users or enterprises.
The amount of information that can flow through a network connection in a given period of time is referred to as bandwidth. Network bandwidth is typically measured in thousands of bits per second (kbps), millions of bits per second (Mbps), billions of bits per second (Gbps) and trillions of bits per second (Tbps). The theoretical bandwidth of a network is an important consideration in network design. If the theoretical bandwidth of a network connection is known, the formula T=S/BW (transfer time = size of file / bandwidth) can be used to calculate potential data transfer time. However the actual bandwidth, referred to as throughput, is affected by multiple factors such as network devices and topology being used, type of data, number of users, hardware and power conditions.
Data can be encoded on analog or digital signals. Analog bandwidth is a measure of how much of the electromagnetic spectrum is occupied by each signal. For instance an analog video signal that requires a wide frequency range for transmission cannot be squeezed into a smaller band. If the necessary analog bandwidth is not available the signal cannot be sent. In digital signaling all information is sent as bits, regardless of the kind of information it is. Unlimited amounts of information can be sent over the smallest digital bandwidth channel.
The concept of layers is used to describe communication from one computer to another. Dividing the network into layers provides the following advantages:
• Reduces complexity
• Standardizes interfaces
• Facilitates modular engineering
• Ensures interoperability
• Accelerates evolution
• Simplifies teaching and learning
Two such layered models are the Open System Interconnection (OSI) and the TCP/IP networking models. In the OSI reference model, there are seven numbered layers, each of which illustrates a particular network function: application, presentation, session, transport, network, data link, and physical. The TCP/IP model has the following four layers: application, transport, Internet, and network access.
Although some of the layers in the TCP/IP model have the same name as layers in the OSI model, the layers of the two models do not correspond exactly. The TCP/IP application layer is equivalent to the OSI application, presentation, and session layers. The TCP/IP model combines the OSI data link and physical layers into the network access layer.
No matter which model is applied, networks layers perform the following five conversion steps in order to encapsulate and transmit data:
1. Images and text are converted to data.
2. The data is packaged into segments.
3. The data segment is encapsulated in a packet with the source and destination addresses.
4. The packet is encapsulated in a frame with the MAC address of the next directly connected device.
5. The frame is converted to a pattern of ones and zeros (bits) for transmission on the media.
This page summarizes the topics discussed in this module.
Computer networks developed in response to business and government computing needs. Applying standards to network functions provided a set of guidelines for creating network hardware and software and provided compatibility among equipment from different companies. Information could move within a company and from one business to another.
Network devices, such as repeaters, hubs, bridges, switches and routers connect host devices together to allow them to communicate. Protocols provide a set of rules for communication.
The physical topology of a network is the actual layout of the wire or media. The logical topology defines how host devices access the media. The physical topologies that are commonly used are bus, ring, star, extended star, hierarchical, and mesh. The two most common types of logical topologies are broadcast and token passing.
A local-area network (LAN) is designed to operate within a limited geographical area. LANs allow multi-access to high-bandwidth media, control the network privately under local administration, provide full-time connectivity to local services and connect physically adjacent devices.
A wide-area network (WAN) is designed to operate over a large geographical area. WANs allow access over serial interfaces operating at lower speeds, provide full-time and part-time connectivity and connect devices separated over wide areas.
A metropolitan-area network (MAN) is a network that spans a metropolitan area such as a city or suburban area. A MAN usually consists of two or more LANs in a common geographic area.
A storage-area network (SAN) is a dedicated, high-performance network used to move data between servers and storage resources. A SAN provides enhanced system performance, is scalable, and has disaster tolerance built in.
A virtual private network (VPN) is a private network that is constructed within a public network infrastructure. Three main types of VPNs are access, Intranet, and Extranet VPNs. Access VPNs provide mobile workers or small office/home office (SOHO) users with remote access to an Intranet or Extranet. Intranets are only available to users who have access privileges to the internal network of an organization. Extranets are designed to deliver applications and services that are Intranet based to external users or enterprises.
The amount of information that can flow through a network connection in a given period of time is referred to as bandwidth. Network bandwidth is typically measured in thousands of bits per second (kbps), millions of bits per second (Mbps), billions of bits per second (Gbps) and trillions of bits per second (Tbps). The theoretical bandwidth of a network is an important consideration in network design. If the theoretical bandwidth of a network connection is known, the formula T=S/BW (transfer time = size of file / bandwidth) can be used to calculate potential data transfer time. However the actual bandwidth, referred to as throughput, is affected by multiple factors such as network devices and topology being used, type of data, number of users, hardware and power conditions.
Data can be encoded on analog or digital signals. Analog bandwidth is a measure of how much of the electromagnetic spectrum is occupied by each signal. For instance an analog video signal that requires a wide frequency range for transmission cannot be squeezed into a smaller band. If the necessary analog bandwidth is not available the signal cannot be sent. In digital signaling all information is sent as bits, regardless of the kind of information it is. Unlimited amounts of information can be sent over the smallest digital bandwidth channel.
The concept of layers is used to describe communication from one computer to another. Dividing the network into layers provides the following advantages:
• Reduces complexity
• Standardizes interfaces
• Facilitates modular engineering
• Ensures interoperability
• Accelerates evolution
• Simplifies teaching and learning
Two such layered models are the Open System Interconnection (OSI) and the TCP/IP networking models. In the OSI reference model, there are seven numbered layers, each of which illustrates a particular network function: application, presentation, session, transport, network, data link, and physical. The TCP/IP model has the following four layers: application, transport, Internet, and network access.
Although some of the layers in the TCP/IP model have the same name as layers in the OSI model, the layers of the two models do not correspond exactly. The TCP/IP application layer is equivalent to the OSI application, presentation, and session layers. The TCP/IP model combines the OSI data link and physical layers into the network access layer.
No matter which model is applied, networks layers perform the following five conversion steps in order to encapsulate and transmit data:
1. Images and text are converted to data.
2. The data is packaged into segments.
3. The data segment is encapsulated in a packet with the source and destination addresses.
4. The packet is encapsulated in a frame with the MAC address of the next directly connected device.
5. The frame is converted to a pattern of ones and zeros (bits) for transmission on the media.
Detailed encapsulation process
Detailed encapsulation process
2.3.7 This page describes the process of encapsulation.
All communications on a network originate at a source, and are sent to a destination. The information sent on a network is referred to as data or data packets. If one computer (host A) wants to send data to another computer (host B), the data must first be packaged through a process called encapsulation.
Encapsulation wraps data with the necessary protocol information before network transit. Therefore, as the data packet moves down through the layers of the OSI model, it receives headers, trailers, and other information.
To see how encapsulation occurs, examine the manner in which data travels through the layers as illustrated in Figure . Once the data is sent from the source, it travels through the application layer down through the other layers. The packaging and flow of the data that is exchanged goes through changes as the layers perform their services for end users. As illustrated in Figure , networks must perform the following five conversion steps in order to encapsulate data:
1. Build the data – As a user sends an e-mail message, its alphanumeric characters are converted to data that can travel across the internet work.
2. Package the data for end-to-end transport – The data is packaged for internet work transport. By using segments, the transport function ensures that the message hosts at both ends of the e-mail system can reliably communicate.
3. Add the network IP address to the header – The data is put into a packet or datagram that contains a packet header with source and destination logical addresses. These addresses help network devices send the packets across the network along a chosen path.
4. Add the data link layer header and trailer – Each network device must put the packet into a frame. The frame allows connection to the next directly-connected network device on the link. Each device in the chosen network path requires framing in order for it to connect to the next device.
5. Convert to bits for transmission – The frame must be converted into a pattern of 1s and 0s (bits) for transmission on the medium. A clocking function enables the devices to distinguish these bits as they travel across the medium. The medium on the physical internet work can vary along the path used. For example, the e-mail message can originate on a LAN, cross a campus backbone, and go out a WAN link until it reaches its destination on another remote LAN.
The Lab Activity will provide an in depth review of the OSI model.
The Interactive Media Activity requires students to complete an encapsulation process flowchart.
This page concludes this lesson. The next page will summarize the main points from the module.
OSI layers / Peer-to-peer communications / TCP/IP model
OSI layers
2.3.4 This page discusses the seven layers of the OSI model.
The OSI reference model is a framework that is used to understand how information travels throughout a network. The OSI reference model explains how packets travel through the various layers to another device on a network, even if the sender and destination have different types of network media.
In the OSI reference model, there are seven numbered layers, each of which illustrates a particular network function. - Dividing the network into seven layers provides the following advantages:
• It breaks network communication into smaller, more manageable parts.
• It standardizes network components to allow multiple vendor development and support.
• It allows different types of network hardware and software to communicate with each other.
• It prevents changes in one layer from affecting other layers.
• It divides network communication into smaller parts to make learning it easier to understand.
In the following Interactive Media Activity, the student will identify the seven layers of the OSI model.
The next page discusses peer-to-peer communications through the OSI model.
Peer-to-peer communications
2.3.5This page explains the concept of peer-to-peer communications.
In order for data to travel from the source to the destination, each layer of the OSI model at the source must communicate with its peer layer at the destination. This form of communication is referred to as peer-to-peer. During this process, the protocols of each layer exchange information, called protocol data units (PDUs). Each layer of communication on the source computer communicates with a layer-specific PDU, and with its peer layer on the destination computer as illustrated in Figure .
Data packets on a network originate at a source and then travel to a destination. Each layer depends on the service function of the OSI layer below it. To provide this service, the lower layer uses encapsulation to put the PDU from the upper layer into its data field. Then it adds whatever headers and trailers the layer needs to perform its function. Next, as the data moves down through the layers of the OSI model, additional headers and trailers are added. After Layers 7, 6, and 5 have added their information, Layer 4 adds more information. This grouping of data, the Layer 4 PDU, is called a segment.
The network layer provides a service to the transport layer, and the transport layer presents data to the internetwork subsystem. The network layer has the task of moving the data through the internetwork. It accomplishes this task by encapsulating the data and attaching a header creating a packet (the Layer 3 PDU). The header contains information required to complete the transfer, such as source and destination logical addresses.
The data link layer provides a service to the network layer. It encapsulates the network layer information in a frame (the Layer 2 PDU). The frame header contains information (for example, physical addresses) required to complete the data link functions. The data link layer provides a service to the network layer by encapsulating the network layer information in a frame.
The physical layer also provides a service to the data link layer. The physical layer encodes the data link frame into a pattern of 1s and 0s (bits) for transmission on the medium (usually a wire) at Layer 1.
The next page describes the TCP/IP reference model.
TCP/IP model
2.3.6 This page discusses the TCP/IP reference model, which is the historical and technical standard of the Internet.
The U.S. Department of Defense (DoD) created the TCP/IP reference model, because it wanted to design a network that could survive any conditions, including a nuclear war. In a world connected by different types of communication media such as copper wires, microwaves, optical fibers and satellite links, the DoD wanted transmission of packets every time and under any conditions. This very difficult design problem brought about the creation of the TCP/IP model.
Unlike the proprietary networking technologies mentioned earlier, TCP/IP was developed as an open standard. This meant that anyone was free to use TCP/IP. This helped speed up the development of TCP/IP as a standard.
The TCP/IP model has the following four layers:
• Application layer
• Transport layer
• Internet layer
• Network access layer
Although some of the layers in the TCP/IP model have the same name as layers in the OSI model, the layers of the two models do not correspond exactly. Most notably, the application layer has different functions in each model.
The designers of TCP/IP felt that the application layer should include the OSI session and presentation layer details. They created an application layer that handles issues of representation, encoding, and dialog control.
The transport layer deals with the quality of service issues of reliability, flow control, and error correction. One of its protocols, the transmission control protocol (TCP), provides excellent and flexible ways to create reliable, well-flowing, low-error network communications.
TCP is a connection-oriented protocol. It maintains a dialogue between source and destination while packaging application layer information into units called segments. Connection-oriented does not mean that a circuit exists between the communicating computers. It does mean that Layer 4 segments travel back and forth between two hosts to acknowledge the connection exists logically for some period.
The purpose of the Internet layer is to divide TCP segments into packets and send them from any network. The packets arrive at the destination network independent of the path they took to get there. The specific protocol that governs this layer is called the Internet Protocol (IP). Best path determination and packet switching occur at this layer.
The relationship between IP and TCP is an important one. IP can be thought to point the way for the packets, while TCP provides a reliable transport.
The name of the network access layer is very broad and somewhat confusing. It is also known as the host-to-network layer. This layer is concerned with all of the components, both physical and logical, that are required to make a physical link. It includes the networking technology details, including all the details in the OSI physical and data link layers.
Figure illustrates some of the common protocols specified by the TCP/IP reference model layers. Some of the most commonly used application layer protocols include the following:
• File Transfer Protocol (FTP)
• Hypertext Transfer Protocol (HTTP)
• Simple Mail Transfer Protocol (SMTP)
• Domain Name System (DNS)
• Trivial File Transfer Protocol (TFTP)
The common transport layer protocols include:
• Transport Control Protocol (TCP)
• User Datagram Protocol (UDP)
The primary protocol of the Internet layer is:
• Internet Protocol (IP)
The network access layer refers to any particular technology used on a specific network.
Regardless of which network application services are provided and which transport protocol is used, there is only one Internet protocol, IP. This is a deliberate design decision. IP serves as a universal protocol that allows any computer anywhere to communicate at any time.
A comparison of the OSI model and the TCP/IP model will point out some similarities and differences.
Similarities include:
• Both have layers.
• Both have application layers, though they include very different services.
• Both have comparable transport and network layers.
• Both models need to be known by networking professionals.
• Both assume packets are switched. This means that individual packets may take different paths to reach the same destination. This is contrasted with circuit-switched networks where all the packets take the same path.
Differences include:
• TCP/IP combines the presentation and session layer issues into its application layer.
• TCP/IP combines the OSI data link and physical layers into the network access layer.
• TCP/IP appears simpler because it has fewer layers.
• TCP/IP protocols are the standards around which the Internet developed, so the TCP/IP model gains credibility just because of its protocols. In contrast, networks are not usually built on the OSI protocol, even though the OSI model is used as a guide.
Although TCP/IP protocols are the standards with which the Internet has grown, this curriculum will use the OSI model for the following reasons:
• It is a generic, protocol-independent standard.
• It has more details, which make it more helpful for teaching and learning.
• It has more details, which can be helpful when troubleshooting.
Networking professionals differ in their opinions on which model to use. Due to the nature of the industry it is necessary to become familiar with both. Both the OSI and TCP/IP models will be referred to throughout the curriculum. The focus will be on the following:
• TCP as an OSI Layer 4 protocol
• IP as an OSI Layer 3 protocol
• Ethernet as a Layer 2 and Layer 1 technology
Remember that there is a difference between a model and an actual protocol that is used in networking. The OSI model will be used to describe TCP/IP protocols.
Students will identify the differences between the OSI model and the TCP/IP model in the Lab Activity.
In the Interactive Media Activity, students will identify the layers of the TCP/IP reference model.
The next page explains the encapsulation process.
Wednesday, November 18, 2009
Using layers / OSI model
Using layers to describe data communication
2.3.2 This page describes the importance of layers in data communication.
In order for data packets to travel from a source to a destination on a network, it is important that all the devices on the network speak the same language or protocol. A protocol is a set of rules that make communication on a network more efficient. For example, while flying an airplane, pilots obey very specific rules for communication with other airplanes and with air traffic control.
A data communications protocol is a set of rules or an agreement that determines the format and transmission of data.
Layer 4 on the source computer communicates with Layer 4 on the destination computer. The rules and conventions used for this layer are known as Layer 4 protocols. It is important to remember that protocols prepare data in a linear fashion. A protocol in one layer performs a certain set of operations on data as it prepares the data to be sent over the network. The data is then passed to the next layer where another protocol performs a different set of operations.
Once the packet has been sent to the destination, the protocols undo the construction of the packet that was done on the source side. This is done in reverse order. The protocols for each layer on the destination return the information to its original form, so the application can properly read the data.
The next page explains the OSI model.
OSI model
2.3.3 This page discusses how and why the OSI model was developed.
The early development of networks was disorganized in many ways. The early 1980s saw tremendous increases in the number and size of networks. As companies realized the advantages of using networking technology, networks were added or expanded almost as rapidly as new network technologies were introduced.
By the mid-1980s, these companies began to experience problems from the rapid expansion. Just as people who do not speak the same language have difficulty communicating with each other, it was difficult for networks that used different specifications and implementations to exchange information. The same problem occurred with the companies that developed private or proprietary networking technologies. Proprietary means that one or a small group of companies controls all usage of the technology. Networking technologies strictly following proprietary rules could not communicate with technologies that followed different proprietary rules.
To address the problem of network incompatibility, the International Organization for Standardization (ISO) researched networking models like Digital Equipment Corporation net (DECnet), Systems Network Architecture (SNA), and TCP/IP in order to find a generally applicable set of rules for all networks. Using this research, the ISO created a network model that helps vendors create networks that are compatible with other networks.
The Open System Interconnection (OSI) reference model released in 1984 was the descriptive network model that the ISO created. It provided vendors with a set of standards that ensured greater compatibility and interoperability among various network technologies produced by companies around the world.
The OSI reference model has become the primary model for network communications. Although there are other models in existence, most network vendors relate their products to the OSI reference model. This is especially true when they want to educate users on the use of their products. It is considered the best tool available for teaching people about sending and receiving data on a network.
In the Interactive Media Activity, students will identify the benefits of the OSI model.
The next page will describe the layers of the OSI model.
2.3.2 This page describes the importance of layers in data communication.
In order for data packets to travel from a source to a destination on a network, it is important that all the devices on the network speak the same language or protocol. A protocol is a set of rules that make communication on a network more efficient. For example, while flying an airplane, pilots obey very specific rules for communication with other airplanes and with air traffic control.
A data communications protocol is a set of rules or an agreement that determines the format and transmission of data.
Layer 4 on the source computer communicates with Layer 4 on the destination computer. The rules and conventions used for this layer are known as Layer 4 protocols. It is important to remember that protocols prepare data in a linear fashion. A protocol in one layer performs a certain set of operations on data as it prepares the data to be sent over the network. The data is then passed to the next layer where another protocol performs a different set of operations.
Once the packet has been sent to the destination, the protocols undo the construction of the packet that was done on the source side. This is done in reverse order. The protocols for each layer on the destination return the information to its original form, so the application can properly read the data.
The next page explains the OSI model.
OSI model
2.3.3 This page discusses how and why the OSI model was developed.
The early development of networks was disorganized in many ways. The early 1980s saw tremendous increases in the number and size of networks. As companies realized the advantages of using networking technology, networks were added or expanded almost as rapidly as new network technologies were introduced.
By the mid-1980s, these companies began to experience problems from the rapid expansion. Just as people who do not speak the same language have difficulty communicating with each other, it was difficult for networks that used different specifications and implementations to exchange information. The same problem occurred with the companies that developed private or proprietary networking technologies. Proprietary means that one or a small group of companies controls all usage of the technology. Networking technologies strictly following proprietary rules could not communicate with technologies that followed different proprietary rules.
To address the problem of network incompatibility, the International Organization for Standardization (ISO) researched networking models like Digital Equipment Corporation net (DECnet), Systems Network Architecture (SNA), and TCP/IP in order to find a generally applicable set of rules for all networks. Using this research, the ISO created a network model that helps vendors create networks that are compatible with other networks.
The Open System Interconnection (OSI) reference model released in 1984 was the descriptive network model that the ISO created. It provided vendors with a set of standards that ensured greater compatibility and interoperability among various network technologies produced by companies around the world.
The OSI reference model has become the primary model for network communications. Although there are other models in existence, most network vendors relate their products to the OSI reference model. This is especially true when they want to educate users on the use of their products. It is considered the best tool available for teaching people about sending and receiving data on a network.
In the Interactive Media Activity, students will identify the benefits of the OSI model.
The next page will describe the layers of the OSI model.
Subscribe to:
Comments (Atom)