OSPF Hello protocol
2.2.6 This page will introduce hello packets and the Hello protocol.
When a router starts an OSPF routing process on an interface, it sends a hello packet and continues to send hellos at regular intervals. The rules that govern the exchange of OSPF hello packets are called the Hello protocol.
At Layer 3 of the OSI model, the hello packets are addressed to the multicast address 224.0.0.5. This address is “all OSPF routers”. OSPF routers use hello packets to initiate new adjacencies and to ensure that neighbor routers are still functioning. Hellos are sent every 10 seconds by default on broadcast multi-access and point-to-point networks. On interfaces that connect to NBMA networks, such as Frame Relay, the default time is 30 seconds.
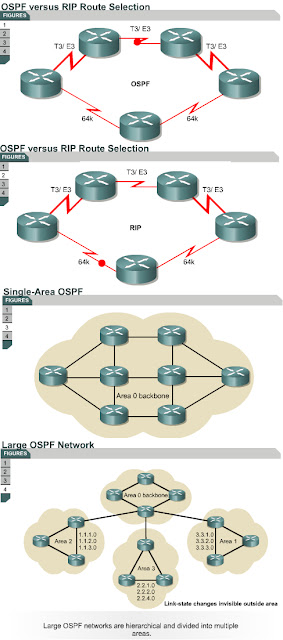
On multi-access networks the Hello protocol elects a designated router (DR) and a backup designated router (BDR).
Although the hello packet is small, it consists of the OSPF packet header. For the hello packet the type field is set to
1.
For the hello packet the type field is set to
1.
The hello packet carries information that all neighbors must agree upon before an adjacency is formed, and link-state information is exchanged.
The Interactive Media Activity will help students identify the fields in an OSPF packet header.
The next page will describe the OSPF routing process.
2.2.6 This page will introduce hello packets and the Hello protocol.
When a router starts an OSPF routing process on an interface, it sends a hello packet and continues to send hellos at regular intervals. The rules that govern the exchange of OSPF hello packets are called the Hello protocol.
At Layer 3 of the OSI model, the hello packets are addressed to the multicast address 224.0.0.5. This address is “all OSPF routers”. OSPF routers use hello packets to initiate new adjacencies and to ensure that neighbor routers are still functioning. Hellos are sent every 10 seconds by default on broadcast multi-access and point-to-point networks. On interfaces that connect to NBMA networks, such as Frame Relay, the default time is 30 seconds.
On multi-access networks the Hello protocol elects a designated router (DR) and a backup designated router (BDR).
Although the hello packet is small, it consists of the OSPF packet header.
The hello packet carries information that all neighbors must agree upon before an adjacency is formed, and link-state information is exchanged.
The Interactive Media Activity will help students identify the fields in an OSPF packet header.
The next page will describe the OSPF routing process.