Summary
This page summarizes the topics discussed in this module.
Redundancy is defined as a duplication of components that allows continued functionality despite the failure of an individual component. In a network, redundancy means to have a backup method to connect all devices. Redundant topologies increase network reliability and decrease downtime caused by a single point of failure.
A redundant switched topology may cause broadcast storms, multiple frame transmissions, and MAC address table instability problems. A broadcast storm is caused by multiple hosts that send and receive multiple broadcast messages. The result is that they continue to propagate broadcast traffic over and over until one of the switches is disconnected. During a broadcast storm, the network appears to be down or extremely slow. Multiple frame transmissions occur when a router receives multiple copies of a frame from multiple switches due to an unknown MAC address. These excessive transmissions cause the router to time out. When a switch incorrectly learns a MAC address of a port, it can cause a loop situation and instability for the MAC address table.
Since switches operate at Layer 2 of the OSI model, all forwarding decisions are made at this level. Layer 2 does not provide a TTL value, which is the set amount of time a packet is provided to reach a destination. The problem is that physical topologies contain switching or bridging loops necessary for reliability, yet a switched network cannot have loops. The solution is to allow physical loops, but create a loop free logical topology.
The loop free logical topology created is called a tree. The topology is a star or extended star that spans the tree of the network. All devices are reachable or spanned. The algorithm used to create this loop free logical topology is the spanning-tree algorithm.
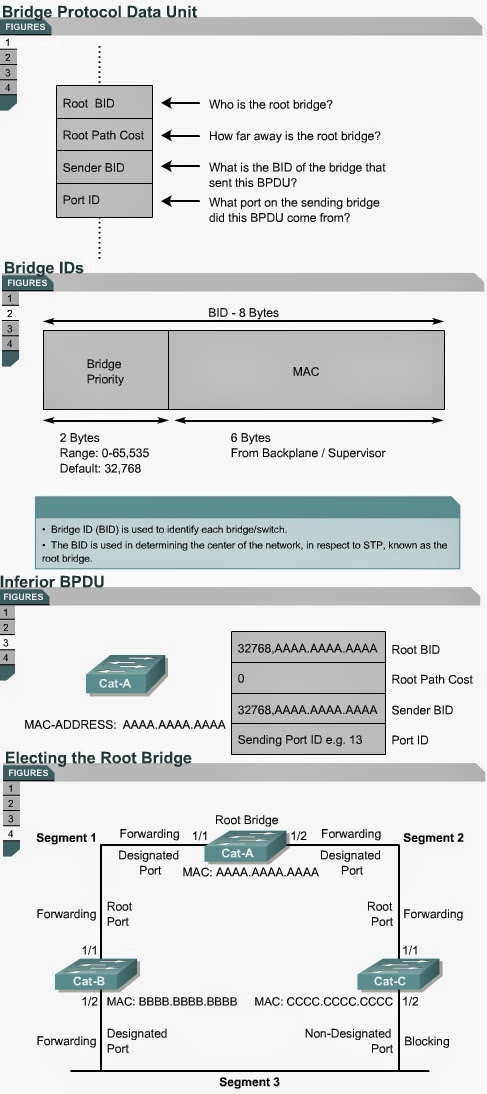
The Spanning-Tree Protocol establishes a root node, called the root bridge. The Spanning-Tree Protocol constructs a topology that has one path for every node on the network. This results in a tree that originates from the root bridge. Redundant links that are not part of the shortest path tree are blocked. It is because certain paths are blocked that a loop free topology is possible. Data frames received on blocked links are dropped.
Switches send messages called the bridge protocol data units (BPDUs) to allow the formation of a loop free logical topology. BPDUs continue to be received on blocked ports. BPDUs contain information that allow switches to perform specific actions:
This page summarizes the topics discussed in this module.
Redundancy is defined as a duplication of components that allows continued functionality despite the failure of an individual component. In a network, redundancy means to have a backup method to connect all devices. Redundant topologies increase network reliability and decrease downtime caused by a single point of failure.
A redundant switched topology may cause broadcast storms, multiple frame transmissions, and MAC address table instability problems. A broadcast storm is caused by multiple hosts that send and receive multiple broadcast messages. The result is that they continue to propagate broadcast traffic over and over until one of the switches is disconnected. During a broadcast storm, the network appears to be down or extremely slow. Multiple frame transmissions occur when a router receives multiple copies of a frame from multiple switches due to an unknown MAC address. These excessive transmissions cause the router to time out. When a switch incorrectly learns a MAC address of a port, it can cause a loop situation and instability for the MAC address table.
Since switches operate at Layer 2 of the OSI model, all forwarding decisions are made at this level. Layer 2 does not provide a TTL value, which is the set amount of time a packet is provided to reach a destination. The problem is that physical topologies contain switching or bridging loops necessary for reliability, yet a switched network cannot have loops. The solution is to allow physical loops, but create a loop free logical topology.
The loop free logical topology created is called a tree. The topology is a star or extended star that spans the tree of the network. All devices are reachable or spanned. The algorithm used to create this loop free logical topology is the spanning-tree algorithm.
The Spanning-Tree Protocol establishes a root node, called the root bridge. The Spanning-Tree Protocol constructs a topology that has one path for every node on the network. This results in a tree that originates from the root bridge. Redundant links that are not part of the shortest path tree are blocked. It is because certain paths are blocked that a loop free topology is possible. Data frames received on blocked links are dropped.
Switches send messages called the bridge protocol data units (BPDUs) to allow the formation of a loop free logical topology. BPDUs continue to be received on blocked ports. BPDUs contain information that allow switches to perform specific actions:
- Select a single switch that
will act as the root of the spanning-tree.
- Calculate the shortest path
from itself to the root switch.
- Designate one of the
switches as the designated switch.
- Choose one of its ports as
its root port, for each non-root switch.
- Select ports that are part
of the spanning-tree. These ports are called designated ports.