VLSM
What is VLSM and why is it used?
1.1.1
Certification-level claim: Compute and use Variable
Length Subnet Masking (VLSM) techniques to design and implement effective and
efficient IP addressing.
This module provides essential background information for the CCNA
exam. Namely, this is how to configure IP addresses, subnet masks and gateway
addresses on routers and hosts, and how to design an IP addressing scheme to
meet design requirements.
Hands-on skills: None
In this lesson students will be introduced to the new topic of
Variable Length Subnet Masks (VLSM). It is important for instructors to
introduce this topic after they have made sure that students are thoroughly
familiar with subnetting. It might be useful to give students the opportunity
to demonstrate their skills at subnetting by giving them a series of small
network addressing problems. These could be such as ones they have done in CCNA
1 and 2. Instructors should then emphasize that VLSM is an important topic and
students will now be able to use subnet zero. During this module, try to give
the students plenty of opportunities to compute and use VLSM techniques to
design and implement effective and efficient IP addressing.
Best practices for teaching this TI include online study with study
guides, group work, practical addressing quizzes using VLSM, lab work, and
mini-lecture.
This is a core TI.
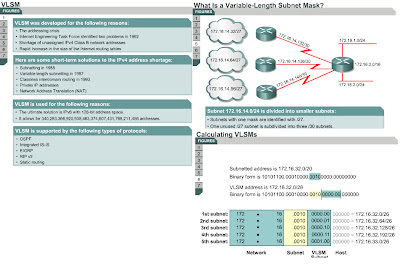
VLSM is simply an extension of basic subnetting, where the same
Class A, B, or C address is subnetted by using masks of different lengths. VLSM
provides a more efficient way of assigning IP addresses. It provides more
flexibility in assigning an adequate number of hosts and subnets given a
limited number of IP addresses. In CCNA 1 and 2, the question may have come up
as to why host addresses are used on a WAN link, which only requires one
address on either end of the link, plus a network address and a broadcast
address. VLSM makes it possible to subnet a subnet so VLSM can be used on WAN
links with a Classless InterDomain Routing (CIDR) notation of /30. IP subnet
zero is enabled by default on Cisco IOS 12.0 and higher. This allows the use of
all zeros and all ones subnets.
Pay particular attention to the following figures:
- Figure outlines that VLSM works with OSPF,
IS-IS, EIGRP, RIP v2, and static routing.
- Figure emphasizes the use of the /30 on the
serial links.
- Figures and illustrate VLSM and how it is computed.
The following are questions for the students to research:
- Why is VLSM
described as subnetting a subnet?
Why was VLSM not used in CCNA 1 and 2?
=====================================
As IP subnets have grown, administrators have looked for ways to
use their address space more efficiently. This page introduces a technique
called VLSM. With VLSM, a network administrator can use a long mask on networks
with few hosts, and a short mask on subnets with many hosts. -
In order to implement VLSM, a network administrator must use a
routing protocol that supports it. Cisco routers support VLSM with Open
Shortest Path First (OSPF), Integrated IS-IS, Enhanced Interior Gateway Routing
Protocol (EIGRP), RIP v2, and static routing.
VLSM allows an organization to use more than one subnet mask
within the same network address space. VLSM implementation maximizes address
efficiency, and is often referred to as subnetting a subnet.
Classful routing protocols require that a single network use the
same subnet mask. As an example, a network with an address of 192.168.187.0 can
use just one subnet mask, such as 255.255.255.0.
A routing protocol that allows VLSM gives the network
administrator freedom to use different subnet masks for networks within a
single autonomous system. Figure shows an example of how a network
administrator can use a 30-bit mask for network connections, a 24-bit mask for
user networks, and even a 22-bit mask for networks with up to 1000 users.
The next page will discuss network address schemes.