UDP operation
10.1.7 This page will explain the similarities and differences between TCP and UDP.
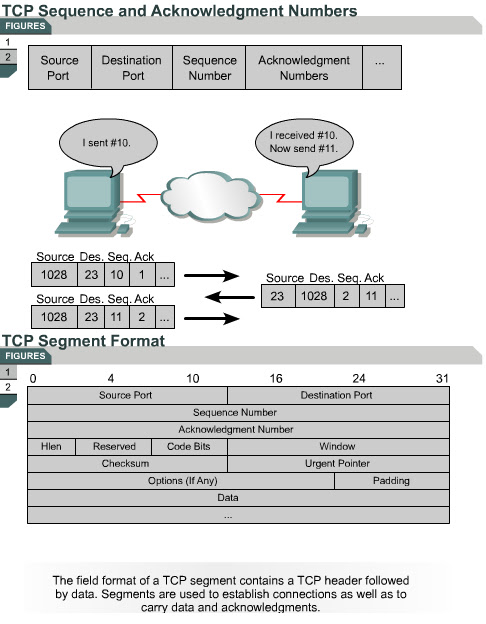
The TCP/IP protocol stack contains many different protocols, each designed to perform a certain task. IP provides Layer 3 connectionless transport through an internetwork. TCP enables connection-oriented, reliable transmission of packets at Layer 4 of the OSI model. UDP provides connectionless, unreliable transmission of packets at Layer 4 of the OSI model.
Both TCP and UDP use IP as their Layer 3 protocol. In addition, TCP and UDP are used by various application layer protocols. TCP provides services for applications such as FTP, HTTP, SMTP, and DNS. UDP is the transport layer protocol used by DNS, TFTP, SNMP, and DHCP.
TCP must be used when applications need to guarantee that a packet arrives intact, in sequence, and unduplicated. The overhead necessary to ensure delivery of a packet is sometimes a problem with TCP. Not all applications need to guarantee delivery of the data packet, so they use the faster, connectionless delivery mechanism afforded by UDP. The UDP protocol standard is described in RFC 768.
UDP does not use windowing or ACKs so application layer protocols must provide error detection.
The Source Port field is an optional field used only if information needs to return to the sending host. When a destination router receives a routing update, the source router is not requesting anything so nothing needs to return to the source. There is no exchange of information or data. The Destination Port field specifies the application to which UDP needs to pass the protocol. A DNS request from a host to a DNS server would have a Destination Port field of 53, the UDP port number for DNS. The Length field identifies the number of octets in the UDP segment. The UDP checksum is optional but should be used to ensure that the data has not been damaged during transmission. For transport across the network, UDP is encapsulated within the IP packet.
Once a UDP segment arrives at the destination IP address, a mechanism must exist which allows the receiving host to determine the exact destination application. Destination ports are used for this purpose. If a host is running both TFTP and DNS services, it must be able to determine what service the arriving UDP segments need. The Destination Port field in the UDP header determines the application to which a UDP segment will be delivered.
This page concludes this lesson. The next lesson will provide an overview of transport layer ports. The first page describes multiple conversations between hosts