Echo messages
8.1.7 This page will provide information about ICMP messages.
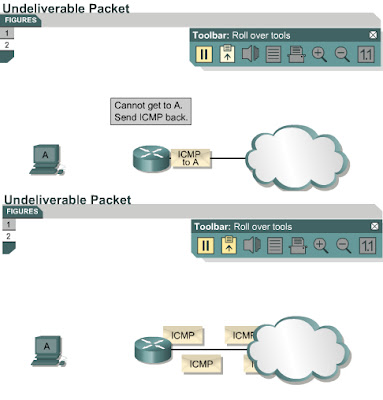
As with any type of packet, ICMP messages have special formats. Each ICMP message type shown in Figure has its own unique characteristics. All ICMP message formats start with the same three fields:
• Type
• Code
• Checksum The type field indicates the type of ICMP message being sent. The code field includes further information specific to the message type. The checksum field, as in other types of packets, is used to verify the integrity of the data.
Figure shows the message format for the ICMP echo request and echo reply messages. The relevant type and code numbers are shown for each message type. The identifier and sequence number fields are unique to the echo request and echo reply messages. The identifier and sequence fields are used to match the echo replies to the corresponding echo request. The data field contains additional information that may be a part of the echo reply or echo request message.
The Interactive Media Activity will test the ability of students to place the ICMP message fields in the correct order.
The next page will explain why destination unreachable messages occur