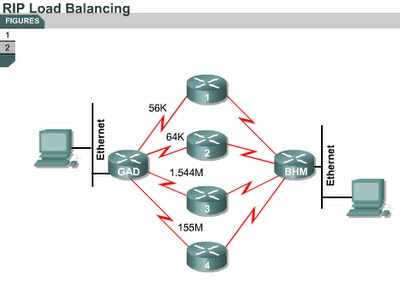
Load balancing across multiple paths
7.2.9 This page will further explain how routers use load balancing to transmit packets to a destination IP address over multiple paths. The paths are derived either statically or with dynamic protocols, such as RIP, EIGRP, OSPF, and IGRP.
When a router learns multiple routes to a specific network, the route with the lowest administrative distance is installed in the routing table. Sometimes the router must select a route from among many, learned through the same routing process with the same administrative distance. In this case, the router chooses the path with the lowest cost or metric to the destination. Each routing process calculates its cost differently and the costs may need to be manually configured in order to achieve load balancing.
If the router receives and installs multiple paths with the same administrative distance and cost to a destination, load-balancing can occur. Cisco IOS imposes a limit of up to six equal cost routes in a routing table, but some IGPs have their own limitations. EIGRP allows up to four equal cost routes.
By default, most IP routing protocols install a maximum of four parallel routes in a routing table. Static routes always install six routes. The exception is BGP, which by default allows only one path to a destination.
The range of maximum paths is one to six paths. To change the maximum number of parallel paths allowed, use the following command in router configuration mode:
Router(config-router)#maximum-paths [number ]
IGRP can load balance up to six unequal links. RIP networks must have the same hop count to load balance, whereas IGRP uses bandwidth to determine how to load balance.
In Figure , there are three ways to reach Network X:
• E to B to A with a metric of 30
• E to C to A with a metric of 20
• E to D to A with a metric of 45
Router E chooses the second path, E to C to A with a metric of 20, since it is a lower cost than 30 and 45.
Cisco IOS supports two methods of load balancing for IP packets. These are per-packet and per-destination load balancing. If process switching is enabled, the router will alternate paths on a per-packet basis. If fast switching is enabled, only one alternate route will be cached for the destination address. All packets that are bound for a specific host will take the same path. Packets bound for a different host on the same network may use an alternate route. Traffic is load balanced on a per-destination basis.
By default the router uses per-destination load balancing, also called fast switching. The route cache allows outgoing packets to be load-balanced on a per-destination basis rather than on a per-packet basis. To disable fast switching, use the no ip route-cache command. Using this command will cause traffic to be load balanced on a per-packet basis.
In the Lab Activities, students will configure and observe load balancing.
The next page will discuss static routes with RIP.