Core layer switches
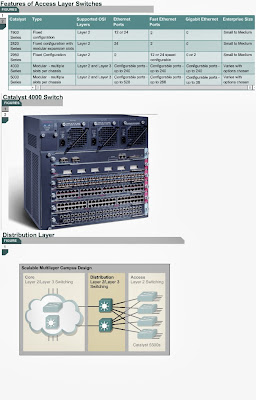
5.2.6 The core layer is the backbone of the campus switched network. The switches in this layer can make use of a number of Layer 2 technologies. Provided that the distance between the core layer switches is not too great, the switches can use Ethernet technology. Other Layer 2 technologies such as ATM cell switching, can also be used. In a network design, the core layer can be a routed, or Layer 3, core. Core layer switches are designed to provide efficient Layer 3 functionality when needed. Factors such as need, cost, and performance should be considered before a choice is made.
The following Cisco switches are suitable for the core layer:
5.2.6 The core layer is the backbone of the campus switched network. The switches in this layer can make use of a number of Layer 2 technologies. Provided that the distance between the core layer switches is not too great, the switches can use Ethernet technology. Other Layer 2 technologies such as ATM cell switching, can also be used. In a network design, the core layer can be a routed, or Layer 3, core. Core layer switches are designed to provide efficient Layer 3 functionality when needed. Factors such as need, cost, and performance should be considered before a choice is made.
The following Cisco switches are suitable for the core layer:
- Catalyst 6500
series
- Catalyst 8500
series
- IGX 8400 series
- Lightstream 1010